Provides containerized deployment options with features like lightweight image, secure non-root user execution, health checks, and environment validation.
Supports environment variable configuration through .env files for managing API keys and other settings.
Offers deployment configuration for Kubernetes with container specifications and secure API key management.
Provides deployment instructions and environment setup specific to Linux environments.
Supports integration with Claude Desktop on macOS through specific configuration file paths and setup instructions.
Implements the MCP server in Python with async/await support and type hints for better performance and code quality.
AbuseIPDB MCP Server (Python)
A Model Context Protocol (MCP) server for integrating with the AbuseIPDB API. This server provides two main functions: checking IP addresses for abuse reports and reporting abusive IP addresses.
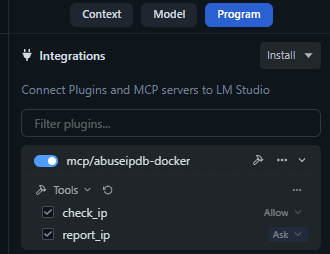
Features
Check IP: Query AbuseIPDB for abuse reports on a specific IP address with verbose details by default
Report IP: Submit abuse reports for malicious IP addresses
Complete Categories Mapping: Full 1-23 category mapping with human-readable names (including DNS Compromise, DNS Poisoning, etc.)
Optimized Return Values: Direct TextContent list returns for better MCP SDK compatibility
Rate Limit Handling: Detailed error messages with retry information
Comprehensive Response Formatting: Clean, readable output without markdown formatting
Input Validation: Robust validation for IP addresses and parameters
Alpine Docker Support: Lightweight deployment and containerization
MCP Configuration: Seamless integration with MCP clients
Async/Await Support: High-performance asynchronous operations
Clean Architecture: Simplified error handling and response structure
Latest MCP SDK: Compatible with MCP SDK 1.12.2+
Recent Updates (v1.2.0)
✅ Fixed MCP SDK Compatibility: Updated to work with MCP SDK 1.12.2
✅ Improved Return Values: Changed from
CallToolResultto directTextContentlist returns✅ Enhanced Categories: Added missing categories 1 (DNS Compromise) and 2 (DNS Poisoning)
✅ Better Default Settings: Verbose mode enabled by default for detailed reports
✅ Cleaner Output: Removed markdown formatting for better readability in MCP clients
✅ Updated Dependencies: Upgraded to latest stable versions
Live Demo
IP Reputation Check and Advanced Analysis
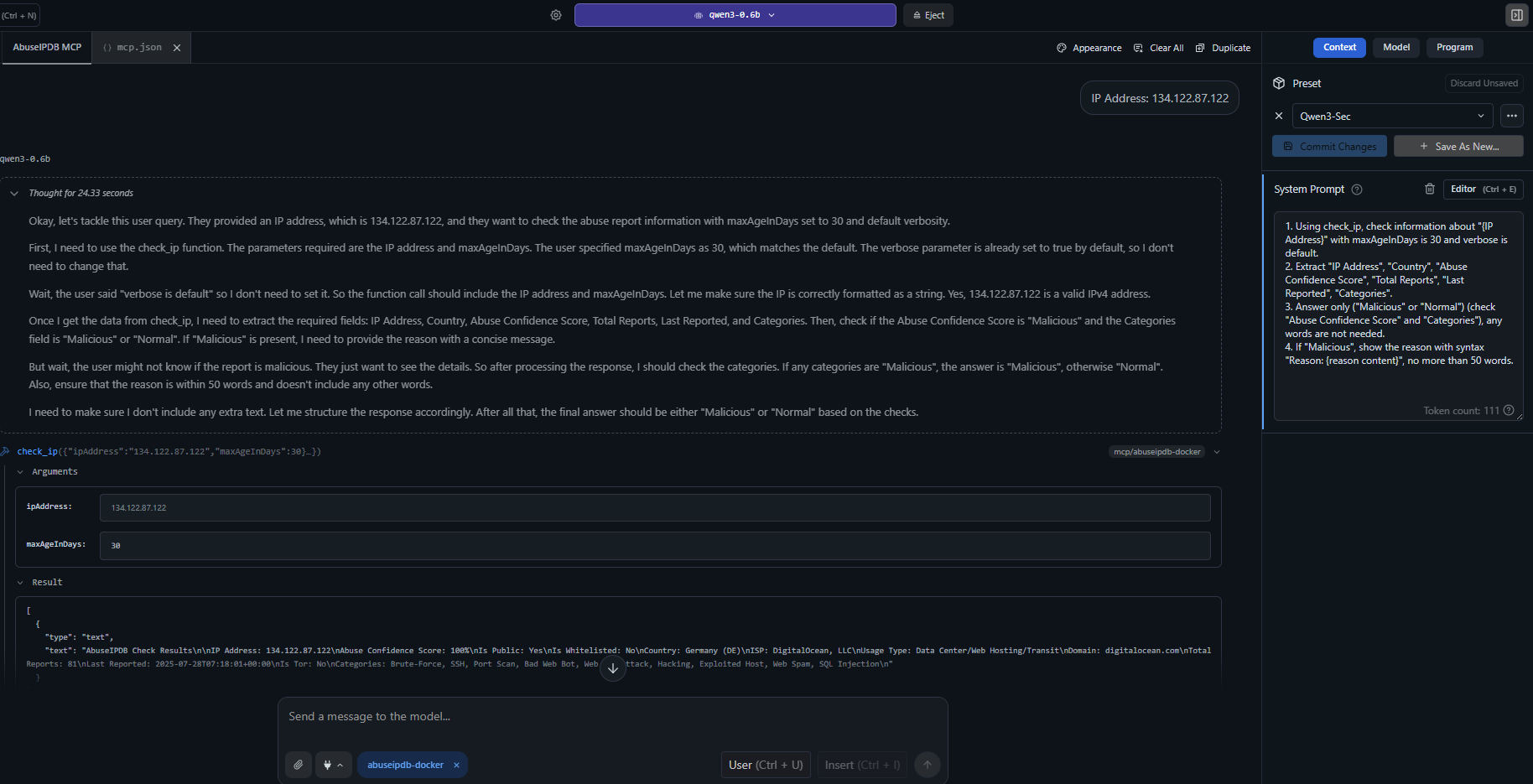
Example showing the
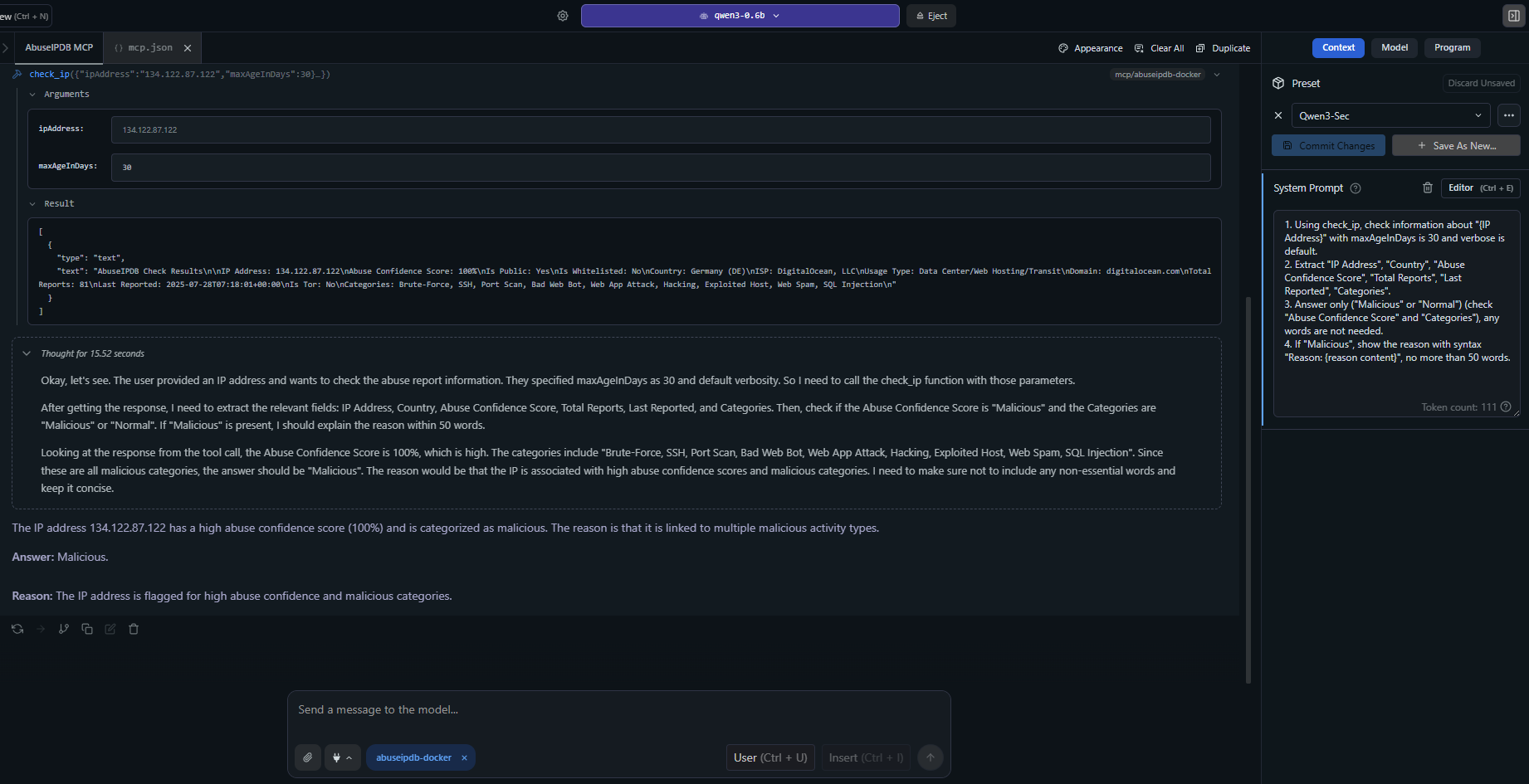
Advanced usage example demonstrating detailed IP analysis with verbose reporting, showing ISP information, abuse confidence scores, and recent attack patterns.
Setup
Prerequisites
Python 3.8 or higher
Docker (for containerized deployment)
An AbuseIPDB API key (get one at abuseipdb.com)
Local Installation
Clone or download this repository
Create a virtual environment:
Install dependencies:
Set your AbuseIPDB API key as an environment variable:
Running the Server
Docker Deployment
Quick Start
Docker Compose
MCP Client Integration
The images above show real examples of the AbuseIPDB MCP server integrated with Claude Desktop, demonstrating IP reputation analysis and threat intelligence capabilities.
Claude Desktop Configuration
Add this to your Claude Desktop claude_desktop_config.json:
Local Python Server
Docker Container
Available Tools
1. check_ip
Check an IP address for abuse reports.
Parameters:
ipAddress(required): IPv4 or IPv6 address to checkmaxAgeInDays(optional): Only return reports within the last x days (1-365, default: 30)verbose(optional): Include detailed reports in the response (default: true)
Example:
Sample Response:
2. report_ip
Report an abusive IP address to AbuseIPDB.
Parameters:
ip(required): IPv4 or IPv6 address to reportcategories(required): Comma-separated category IDs (e.g., "18,22")comment(optional): Descriptive text of the attack (no PII)timestamp(optional): ISO 8601 datetime of the attack
Available Categories:
1: DNS Compromise
2: DNS Poisoning
3: Fraud Orders
4: DDoS Attack
5: FTP Brute-Force
6: Ping of Death
7: Phishing
8: Fraud VoIP
9: Open Proxy
10: Web Spam
11: Email Spam
12: Blog Spam
13: VPN IP
14: Port Scan
15: Hacking
16: SQL Injection
17: Spoofing
18: Brute-Force
19: Bad Web Bot
20: Exploited Host
21: Web App Attack
22: SSH
23: IoT Targeted
Example:
Error Handling
The server handles various error conditions:
Rate Limits: HTTP 429 responses with retry information
Invalid API Keys: Clear authentication error messages
Invalid IP Addresses: Format validation with helpful messages
API Errors: Detailed error responses with status codes
Network Issues: Timeout and connection error handling
Rate Limits
AbuseIPDB has the following daily rate limits:
Plan | Check Endpoint | Report Endpoint |
Free | 1,000 | 100 |
Basic | 3,000 | 300 |
Premium | 10,000 | 1,000 |
Enterprise | 100,000 | 10,000 |
The server automatically handles rate limit responses and provides retry information.
Dependencies
mcp: 1.12.2+ - Model Context Protocol SDK
httpx: 0.27.0+ - Async HTTP client
pydantic: 2.8.0+ - Data validation
python-dotenv: 1.0.0+ - Environment variable loading
Project Structure
Testing
Run the comprehensive test suite:
Test Docker deployment:
Recent Fixes (v1.2.0)
MCP SDK Compatibility
Fixed: Updated to MCP SDK 1.12.2 for better compatibility
Fixed: Changed return values from
CallToolResultobjects to directTextContentlistsFixed: Resolved validation errors with newer MCP SDK versions
Enhanced Features
Added: Complete category mapping (1-23) including DNS Compromise and DNS Poisoning
Improved: Default verbose mode for more detailed responses
Enhanced: Cleaner output formatting without markdown for better MCP client compatibility
Updated: All dependencies to latest stable versions
Docker Improvements
Optimized: Alpine-based Docker image for smaller footprint
Simplified: Removed unnecessary health checks and complex configurations
Streamlined: Better build process and dependency management
Troubleshooting
Common Issues
"API key required" error: Ensure
ABUSEIPDB_API_KEYenvironment variable is setConnection timeout: Check network connectivity and firewall settings
Rate limit exceeded: Wait for the retry period or upgrade your AbuseIPDB plan
Invalid IP format: Ensure IP addresses are properly formatted IPv4 or IPv6
Docker Testing
Test the server inside Docker:
MCP Client Issues
If you experience issues with MCP clients:
Verify MCP configuration: Check your
claude_desktop_config.jsonsyntaxTest server directly: Run the Python server and send JSON-RPC messages manually
Check logs: Look for error messages in your MCP client logs
Version compatibility: Ensure you're using MCP SDK 1.12.2+
Contributing
Fork the repository
Create a feature branch
Make your changes
Add tests for new functionality
Submit a pull request
Screenshots & Demo
The screenshots in this README demonstrate real-world usage of the AbuseIPDB MCP server:
MCP Integrations Overview: Shows how the server integrates with MCP-compatible clients
Live IP Analysis: Real examples of IP reputation checks with detailed threat intelligence
Interactive Usage: Demonstrates the conversational interface when used with AI assistants like Claude
These examples showcase the server's ability to provide comprehensive cybersecurity intelligence through natural language interactions, making IP reputation analysis accessible and actionable for security professionals and developers.
License
This project is licensed under the MIT License - see the LICENSE file for details.
What this means:
✅ Free to use for personal and commercial projects
✅ Modify and distribute the code as needed
✅ No warranty - use at your own risk
✅ Attribution - keep the copyright notice when redistributing
The MIT License is one of the most permissive open source licenses, making this project easy to integrate into your cybersecurity toolkit.
Made with ❤️ for the MCP community
This server cannot be installed
remote-capable server
The server can be hosted and run remotely because it primarily relies on remote services or has no dependency on the local environment.
Integrates with the AbuseIPDB API to check IP addresses for abuse reports and report abusive IP addresses.
Related MCP Servers
- -securityFlicense-qualityProvides IP geolocation services using IP-API.com without requiring an API key, enabling users to obtain detailed location and network information for any IP address in a clean, formatted output.Last updated -13
- AsecurityAlicenseAqualityProvides access to Shodan API functionality, enabling AI assistants to query information about internet-connected devices for cybersecurity research and threat intelligence.Last updated -2329MIT License
- AsecurityAlicenseAqualityProvides blockchain address risk scoring and asset information through the BICScan API, allowing users to assess risks for crypto addresses, domains, and dApps on a scale of 0-100.Last updated -210MIT License
- AsecurityAlicenseAqualityLook up IP address geolocation, network information, detect proxies and VPNs, and find abuse contact details using IPLocate.ioLast updated -6259MIT License